Mastering the Art of Web Exploitation || Tips to streamline your coding journey
You’ve discovered a web vulnerability, now comes the exciting part: crafting a proof of concept (POC) to demonstrate its exploitability! With the right tips and tricks at your disposal, you can streamline your coding process and deliver a robust POC in no time. This not only empowers organizations to identify and address their security weaknesses but also enhances their overall security posture once the vulnerability is resolved. Ready to accelerate your coding journey? Dive into the following strategies that will help you code faster and more efficiently, ensuring your valuable insights lead to meaningful improvements in cybersecurity!
Code faster (web)exploits
While coding exploits can be an exhilarating challenge, the repetitive nature of the process can often feel tedious. In this article, I’ll share some practical tips and strategies designed to streamline your workflow and make your life easier as you tackle the complexities of Advanced Web Attacks and Exploitation (AWAE), also known as OSWE. By implementing these insights, you can enhance your efficiency, reduce frustration, and focus more on the fun aspects of coding. Let’s dive in and discover how to elevate your web exploitation skills while keeping the excitement alive!
Generate a quick code for for a POC with curlconverter
Imagine you have found a web vulnerability and now you want to automate it to a automatoc exploit. But coding takes some time and as usual Burp Suite should have been running while working on a web application to intercept all traffice between your machine and the web application.
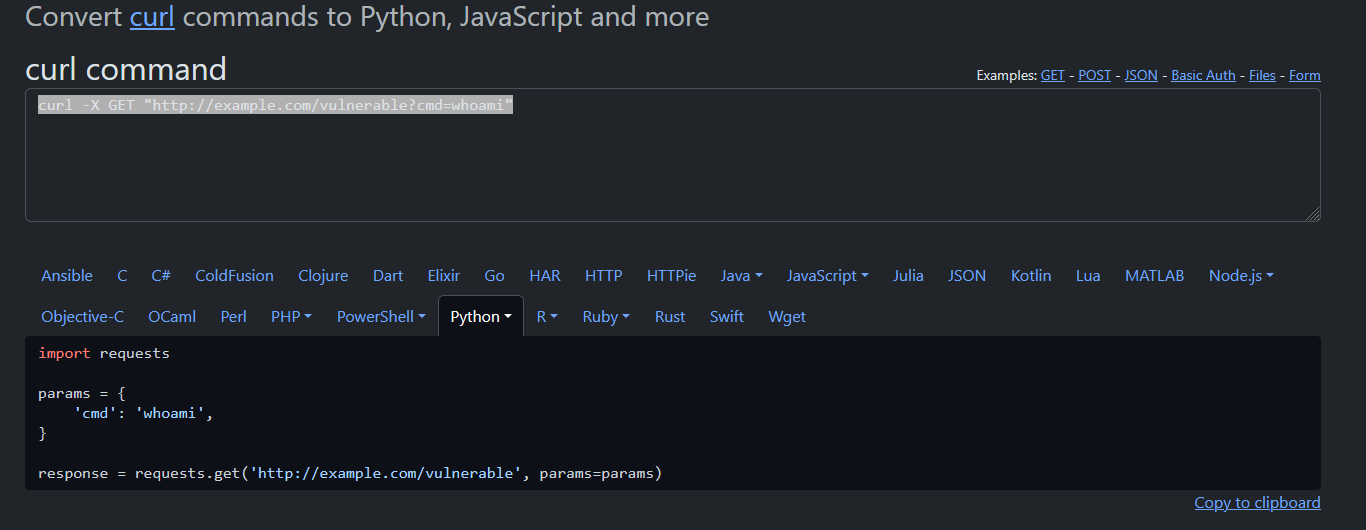
Now select the intercepted requests via Burp Suite. Copy the request via Right mouse click > Copy as curl command (bash). Paste the content on this website, it will generate a quick python script of the request For example the following curl command has been copied from Burp Suite.
1
curl -X GET "http://example.com/vulnerable?cmd=whoami"
This can be converted on the curlconverter.com to several languagues and would help you get starting write your exploit.
Consider that sharing information might be a risk!
Sharing information on a web form that is not owned by you can pose several significant risks, including:
- Lack of Control Over Information: Once you share information on a third-party platform, you lose control over how it is used, shared, or disseminated, which can lead to unintended consequences.
- Increased Risk of Exploitation: By sharing details about vulnerabilities, you may inadvertently provide malicious actors with the information they need to exploit those vulnerabilities, potentially leading to widespread attacks.
- Loss of Trust: If you are associated with a community or organization, sharing vulnerabilities irresponsibly can damage your reputation and the trust others place in you.
- Potential for Misuse: Even if your intentions are good, the information you share could be misused by others for malicious purposes, leading to harm to individuals or organizations.
In summary, it’s crucial to handle information about vulnerabilities responsibly and ethically, ensuring that you have the proper permissions and are following legal and ethical guidelines before sharing such information.
It’s better to have a local version running if you working on something that should be kept safe (and private). Lucky for us there is a Github page available with instruction to install it on your machine.
Install curlconverter locally
First we should install NPM if it is not installed yet.
1
sudo apt install npm
Next we can install curlconverter with the following command.
1
npm install --global curlconverter
Usage curlconverter from the terminal
Since a curl command example has been shared previously we use the same one to generate a python script within the terminal. Don’t forget the - at the end of the command, it is required to read from stdin.
1
echo 'curl -X GET "http://example.com/vulnerable?cmd=whoami"' | curlconverter --language python -
The output should look like this:
1
2
3
4
5
6
7
8
9
┌──(emvee㉿kali)-[~]
└─$ echo 'curl -X GET "http://example.com/vulnerable?cmd=whoami"' | curlconverter --language python -
import requests
params = {
'cmd': 'whoami',
}
response = requests.get('http://example.com/vulnerable', params=params)
Copy As Python-Requests in Burp Suite
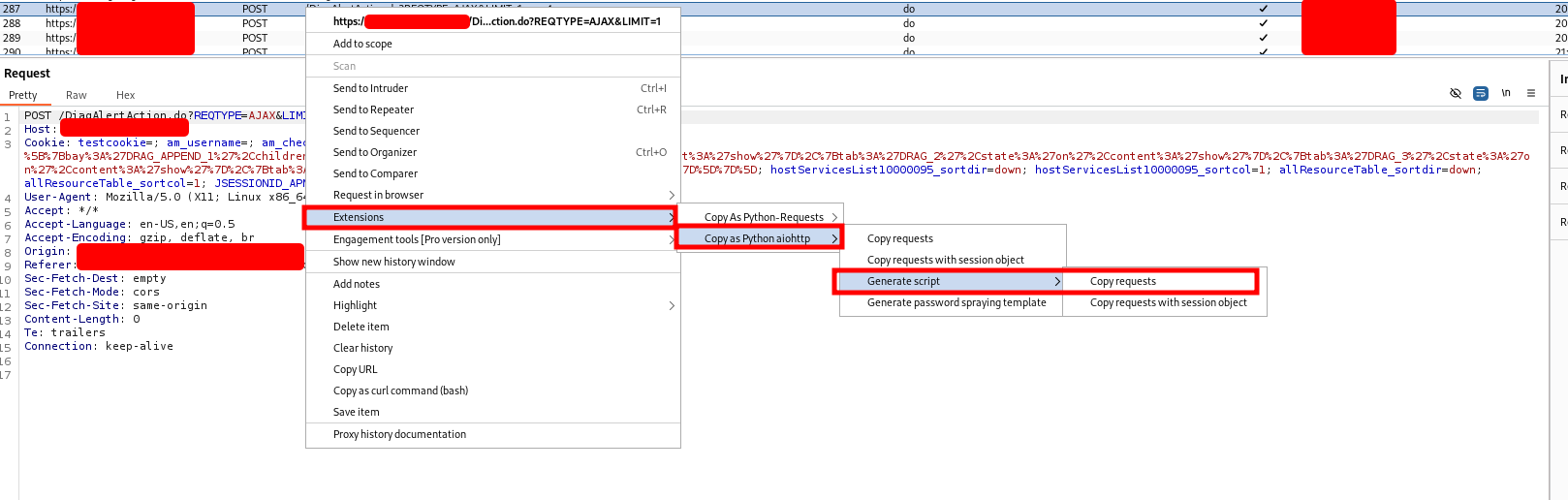
As mentioned above, Burp Suite should always be active while working on a web application to intercept requests. This will help you inspect requests and responses in to and from the web application. besides it will help you as well with sending requests to Burp Intruder or Burp Repeater, it gives you the ability to use extensions installed in Burp Suite to craft for example a Python code based on a request. One of those extensions is Copy as Python aiohttp. There are several useful extensions available in the Portswigger Bapp Store, in this article just one of them will be explained.
Install extension
Installing an extension is pretty easy, you just have to follow the next steps:
- Open tab
Extensionsin Burp Suite - Click on
BApp Storetab - Search for
Copy As Pythonand click install
Use the extension
It is easy in use as well, see the following steps (including the screenshot).
- Select the intercepted request.
Right mouse click>Extensions>Copy As Python-Requests aiohttp
After copying the code, you can paste it in your exploit and start working on your POC.
Use your own user snippets in Visual Studio Code
As you progress in your journey of developing web exploits, you’ll generate a significant amount of code that can frequently be reused in various projects. To enhance your efficiency, consider leveraging user code snippets in Visual Studio Code. This handy feature allows you to store and quickly retrieve your most commonly used code snippets, making your coding process smoother and more productive.
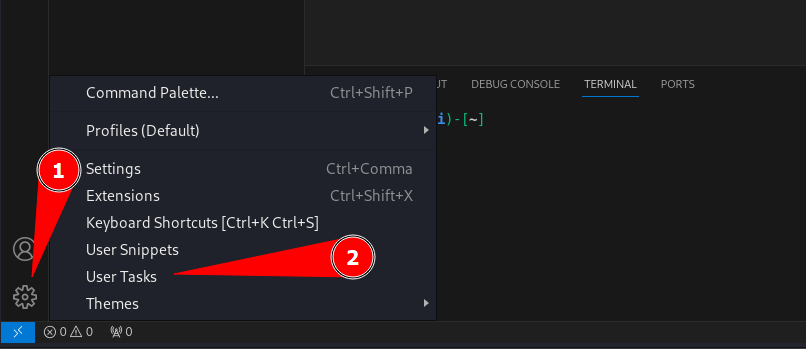
To configure the user snippets in Visual Studio you have to click on the configuration wheel followed by the menu option User snippets.
A new pop-up window will show. In this window you have to search for one of the programming languagues you will use. In this example for developing web exploits Python is being used.
A simple request with just one user code snippet that can be called with httpRequest
1
2
3
4
5
6
7
8
9
10
11
12
13
14
{
"Simple HTTP Request": {
"prefix": "httpRequest",
"body": [
"import requests",
"",
"url = \"${1:http://example.com}\"",
"response = requests.get(url)",
"print(response.status_code)",
"print(response.text)"
],
"description": "Create a simple HTTP GET request to a website."
}
}
An example of a user code snipppet with multiple code snippets httpRequest and printRequestContent.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
{
"Simple HTTP Request": {
"prefix": "httpRequest",
"body": [
"import requests",
"",
"url = \"${1:http://example.com}\"",
"response = requests.get(url)",
"print(response.status_code)",
"print(response.text)"
],
"description": "Create a simple HTTP GET request to a website."
}
"Function to Print Request Content": {
"prefix": "printRequestContent",
"body": [
"import requests",
"",
"def print_request_content(url):",
" response = requests.get(url)",
" print(response.status_code)",
" print(response.text)",
"",
"# Example usage:",
"print_request_content(\"${1:http://example.com}\")"
],
"description": "Define a function to print the content of a request."
}
}
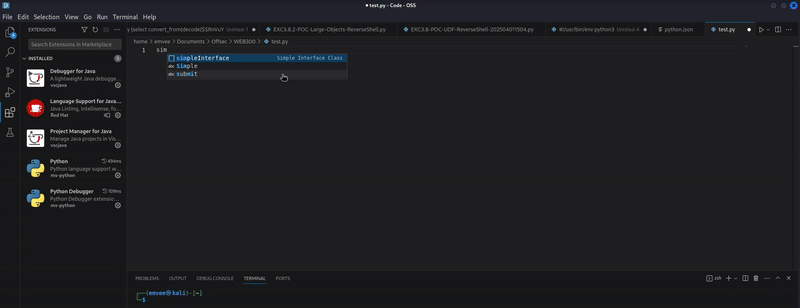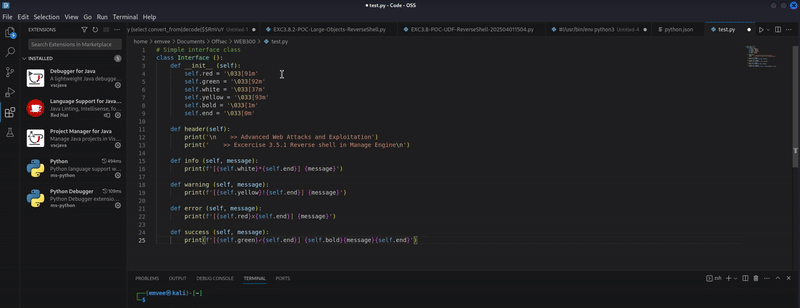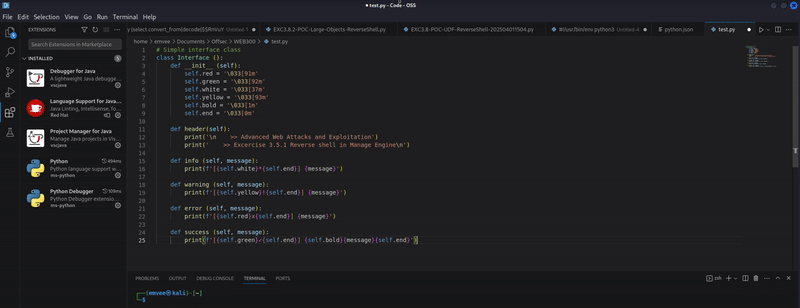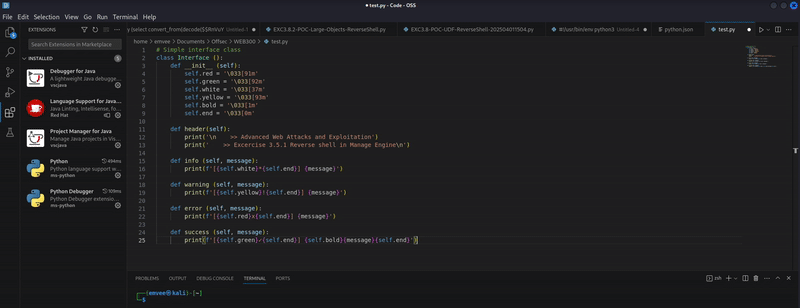
As soon as you have saved your code snippets in the python.json file you can use the prefix name to import your code snippet into your project. For example in the image below you can see how I import my code snippet with the name simpleInterFace and autocomplete with hitting the TAB or ENTER key.
Conclusion
In summary, as you explore the realm of web exploit development, it’s essential to wield your skills ethically and responsibly. With the power to uncover vulnerabilities comes the opportunity to educate and uplift the community. Share your insights in creative and enjoyable ways, encouraging collaboration and growth. By doing so, you not only enhance your own expertise but also contribute to a safer and more secure digital environment for all. Together, we can build a stronger, more secure future!